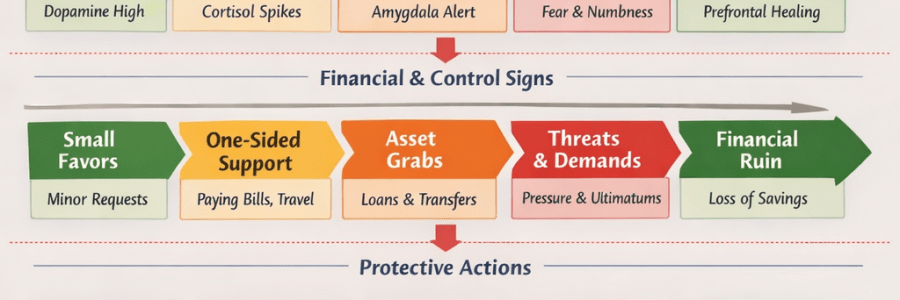
Emerging patterns and technological abuse
🚨 A violent incident in Spain 🧑⚖️ Policy debate in Spain ⚖️ France — domestic violence systems under review 🪪 Broader European context (recent data and debates) EU-level commitment and legal framework Statistical trends Calls for prevention and early intervention Controversies around withdrawal from protections 📊 Social dynamics and reporting Under‑reporting remains a concern Feminicide studies 📌 Takeaway… Read More Emerging patterns and technological abuse